Well, events 1030 and 1058 are very generic errors and can be caused by one of many different reasons. I often see questions at Experts Exchange on how to overcome these events. I don't have all the answers, but have helped out a lot of people diagnose and fix these events.
Explore Experts Exchange Articles
Our articles are written by a community of IT professionals and experts to provide insight on trending topics and common technology roadblocks.
Get AccessGet Access
Access our full library of articles written by our technology community. Read how-to guides, new perspectives on trending tech, and exclusive insights on industry news.
Articles For You
-
F248 Service Code Errors - Kyocera PrintersGenerally, an F248 error code will be caused by incorrect drivers on a Windows computer. Ensuring you have correct drivers installed and are not using Microsoft IPP Class Drivers and are not using a WSD port, are the most common solutions. This can also apply to non-Windows clients.
-
"Dirtied Form" in VB.NETMisAccess has a form property to determine if any controls on a form are changed. This property is called “Dirty”. Use of the Dirty property in MsAccess determines whether the current record has been modified since it was last saved. Read/write Boolean. I was unable to find a property in VB.NET
-
Part 6 - Build an immutable backup repository for Veeam Backup & Replication.For Veeam Backup & Replication, this guide will show you, step by step, how to create and implement a disk-based immutable backup repository from scratch.. In this part: Backup of the Linux server itself.
-
How the CISO Can Build Support from Senior ManagementImportance of appropriate Senior Management support for Cybersecurity and what is required to elicit the desired support. Article initially published by ISACA at below ink: https://www.isaca.org/resources/news-and-trends/isaca-now-blog/2021/how-the-ciso-can-build-support-from-senior-management
-
Blank Page Screen In OWA/EAC Exchange 2013/2016/2019 ServerThis article will help you fix blank screen when you try to login to EAC or OWA.
-
Data Center Security Solutions – Is Your DC Safe From Attacks?It is impossible to stop security attacks on data centers. But, we can protect crucial information by opting for resilient data center security solutions. This guide is all about the different types of data center security measures a company can use to secure people's data.
-
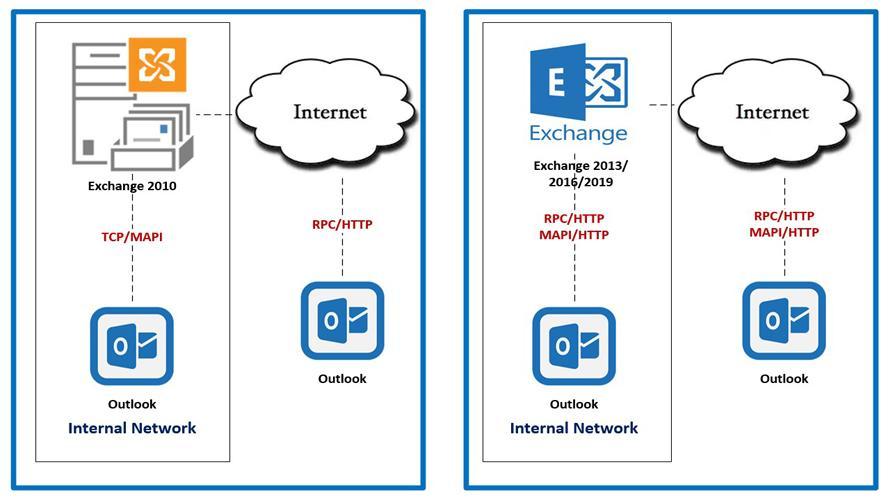
Enable or disable Outlook Anywhere (RPC-HTTP/MAPI-HTTP) in Exchange Server.This article will help to do the below tasks. 1. Disable Outlook Anywhere for single mailbox. 2. Disable Outlook Anywhere for all mailboxes in the organization. 3. Enable Outlook Anywhere for single mailbox. 4. Enable Outlook Anywhere for all mailboxes in the organization.
-
Converting BYTES to CHAR on Oracle databaseIn this article, I will be sharing the issues that we faced while converting the data type and NLS semantic to CHAR from BYTES. This was one of the business use cases where we needed to convert the entire columns throughout the schema from BYTES to CHAR types only for VARCHAR2 columns datatypes.
Newest Articles
-
Improve Network Security – Separate DNS from Active DirectoryWhile deploying Active Directory with integrated DNS makes managing a domain easier, it does come with security risks. Separating out DNS can actually improve security and make things harder for a threat actor.
-
Stopping Backdoor Spam On Microsoft M365As organizations move from an on premises Exchange environment SaaS based M365. There are configurations that may allow email to slip in passed typical email filtering systems. This is all based on the configuration and described in this article, along with the solution.
-
Lessons Learned: Adding Used NVME Drive to HP ProLiant Server with ESXiInstalling used hardware in a home lab or other systems can have some challenges. Hopefully, the lesson learned here with a used NVMe drive will save someone else time and headache.
-
Exchange & Powershell is a Long HistoryA long time ago, Experts-Exchange asked me to write a little article about some Exchange interesting Powershell commands. But I was never able to finish it properly. Here is the result of this work. Exchange has been the first Microsoft product that really needed Powershell to work!
Featured Author
-
Azure Resource Locks: A Key Component of Cloud GovernanceThis article delves into the important characteristic that useful resource locks play in preserving control and making sure compliance in your Azure cloud resources.
-
What are the types of flows in Power Automate?This post provides an overview of Power Automate flow types and how to use them.
Popular Articles
-
WARNING: 5 Reasons why you should NEVER fix a computer for free.It is in our nature to love the puzzle. We are obsessed. The lot of us. We love puzzles. We love the…
-
How Do I Know What to Charge as an IT Consultant?[This article first appeared as "Why are IT services so expensive?" in my first attempt at a blog. …
-
Why you shouldn't use PST filesThey have been around for years and for thousands of Microsoft Outlook users and email …
-
Migrate Small Business Server 2003 to Exchange 2010 and Windows 2008 R2This guide is intended to provide step by step instructions on how to migrate from Small Business …
-
Outlook continually prompting for username and passwordThere have been a lot of questions recently regarding Outlook prompting for a username and password …
Join a collaborative community of technology professionals.