Well, events 1030 and 1058 are very generic errors and can be caused by one of many different reasons. I often see questions at Experts Exchange on how to overcome these events. I don't have all the answers, but have helped out a lot of people diagnose and fix these events.
Explore Experts Exchange Articles
Our articles are written by a community of IT professionals and experts to provide insight on trending topics and common technology roadblocks.
Get AccessGet Access
Access our full library of articles written by our technology community. Read how-to guides, new perspectives on trending tech, and exclusive insights on industry news.
Articles For You
-
Securing Active Directory Domain ControllersIt is more important than ever to ensure that your domain controllers are as secured as possible. This article walks you through a number of settings and procedures to harden your domain controllers.
-
Free in-place upgrade of Nuance PaperPort Professional 14.5 to Kofax PaperPort Professional 14.7Earlier this year, Kofax acquired Nuance's Document Imaging Division, which included PaperPort. Kofax recently released the first version of PaperPort under its stewardship — V14.7. This article explains Kofax's method for upgrading from PaperPort Professional 14.5 to Professional 14.7 at no cost.
-
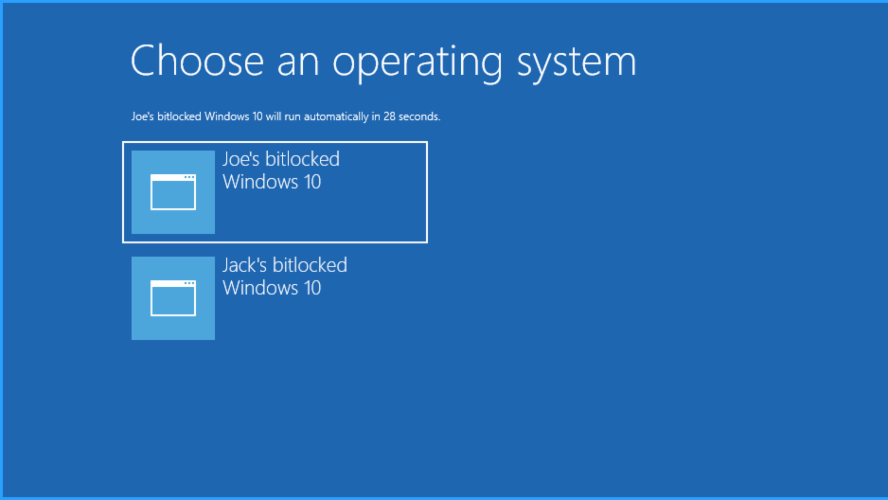
Bitlocker and multi-bootingIf you are asking yourself "will Bitlocker allow me to install several encrypted instances of windows 10 on the same drive?", here is your answer.
-
Join (concat) values from one field from a table or queryAs you can union records, you can join field values. Presented here, DJoin offers increased speed and flexibility compared to the ancient ConcatRelated and similar functions. Further, it offers better read-out of Multi-Value fields.
-
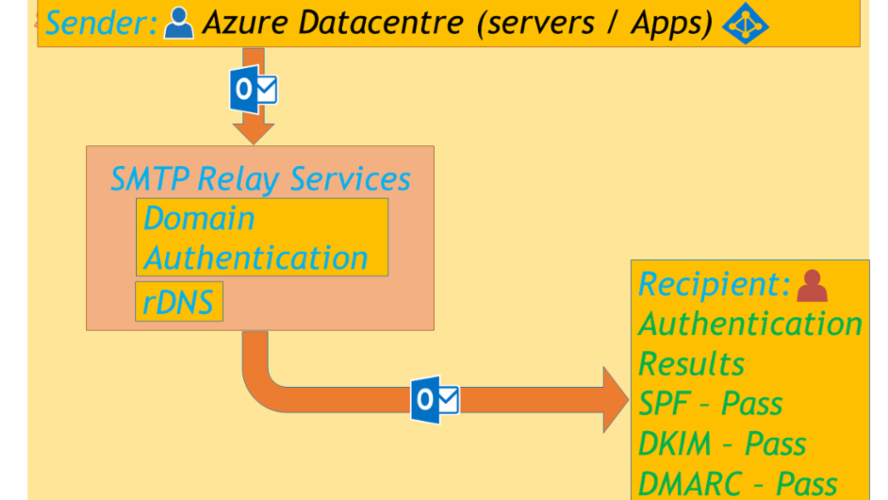
Azure SMTP Restrictions & Resolution with SMTP Relay ServicesThis post explains how Microsoft has strengthened Azure platform security against unauthenticated SMTP traffic to maintain Azure IP stack reputation and how 3rd party SMTP API can be used to overcome these restrictions.
-
CA Validity Period Extension and CA Certificate Renewal ProcessThis article outlines the Importance of Certificate Authority validity period and its impact on Certificate Renewal Process. The article also details out CA certificate renewal process along with CA validity period extension.
-
3 Ways to Assess the Working of Your Magento WebsiteDo you face issues with your Magento e-commerce website? If yes, you need to assess its health and resolve the issues. Go through this article, you might be able to assess the problems and know what to do.
Newest Articles
-
Improve Network Security – Separate DNS from Active DirectoryWhile deploying Active Directory with integrated DNS makes managing a domain easier, it does come with security risks. Separating out DNS can actually improve security and make things harder for a threat actor.
-
Stopping Backdoor Spam On Microsoft M365As organizations move from an on premises Exchange environment SaaS based M365. There are configurations that may allow email to slip in passed typical email filtering systems. This is all based on the configuration and described in this article, along with the solution.
-
Lessons Learned: Adding Used NVME Drive to HP ProLiant Server with ESXiInstalling used hardware in a home lab or other systems can have some challenges. Hopefully, the lesson learned here with a used NVMe drive will save someone else time and headache.
-
Exchange & Powershell is a Long HistoryA long time ago, Experts-Exchange asked me to write a little article about some Exchange interesting Powershell commands. But I was never able to finish it properly. Here is the result of this work. Exchange has been the first Microsoft product that really needed Powershell to work!
Featured Author
-
Git 101Git can be a complicated version control system for beginners, but it definitely is one of the best …
-
How to Make Javascript Talk to PHPOne question that comes up again and again on the PHP section of Experts Exchange is, "How can I …
Popular Articles
-
WARNING: 5 Reasons why you should NEVER fix a computer for free.It is in our nature to love the puzzle. We are obsessed. The lot of us. We love puzzles. We love the…
-
How Do I Know What to Charge as an IT Consultant?[This article first appeared as "Why are IT services so expensive?" in my first attempt at a blog. …
-
Why you shouldn't use PST filesThey have been around for years and for thousands of Microsoft Outlook users and email …
-
Migrate Small Business Server 2003 to Exchange 2010 and Windows 2008 R2This guide is intended to provide step by step instructions on how to migrate from Small Business …
-
Outlook continually prompting for username and passwordThere have been a lot of questions recently regarding Outlook prompting for a username and password …
Join a collaborative community of technology professionals.